For the last 20 years, Cyber Security professionals and government organisations have used the month of October to raise people’s awareness of the threats cyber criminals pose. Releasing resources, reports and information to help organisations and individuals educate and protect themselves from the new techniques criminals and bad actors use for financial reward.
In this blog, we aim to explain what these terms mean when it comes to identity fraud and scam emails.
Business Email Compromise (BEC)
The National Cyber Security Centre (NCSC) defines Business Email Compromise (BEC) as:
“A form of phishing attack where a criminal attempts to trick a senior executive (or budget holder) into transferring funds, or revealing sensitive information. . The criminals behind BEC send convincing-looking emails that might request unusual payments, or contain links to ‘dodgy’ websites. Some emails may contain viruses disguised as harmless attachments, which are activated when opened. Unlike standard phishing emails that are sent out indiscriminately to millions of people, BEC attacks are crafted to appeal to specific individuals, and can be even harder to detect. BEC is a threat to all organisations of all sizes and across all sectors, including non-profit organisations and government.” NCSC BEC infographic
Phishing and Spear-phishing
Phishing is a type of social engineering designed to steal, data, infect computers and gain access to corporate networks. This cyber crime has been around for many years, criminals use deceptive emails, websites and text messages to steal corporate information for financial gain. These criminals use tactics like email addresses to be mistaken as authentic such as security@paypal.admin.com.
Different types of phishing are:
Content injection – A webpage made to look like a familiar vendor or organisation, which contains malicious content that could include a link, form or pop-up that urges the viewer to confirm personal or confidential information.
CEO fraud – This requires domain spoofing which masquerades emails as coming from the CEO or another senior leader within the organisation. The email could ask to transfer funds, purchase gift cards or send tax information.
Email – Most common tactic. Can be sent to many recipients asking them to update information, verify accounts or change passwords.
Fake websites – Websites that look just the same as popular websites, but the domain (URL) is slightly different.
Spear phishing – This advanced targeting email has a criminal focus on one person or organisation. Using highly-personalised messages to steal data that can severely compromise the organisation.
Malware and Malvertising – A person inadvertently installs software that mines the computer or network for information. The criminal uses online ads or pop-ups to trick the viewer into clicking on a link that installs malware on a computer.
Man-in-the-middle – This tricks two people into sending information to each other but one is a criminal faking the requests from each party. The people involved believe they are talking with each other and have no idea a third party is manipulating them.
Smishing
Scammers use text messaging (smishing) to impersonate a person or organisation in a similar way to phishing emails. Tactics used in smishing include:
Fake link tactic – The sender pretends to be a valid organisation and sends a text/SMS message with a link with text to urge the reader to take urgent action by clicking on the link.
Convincing phone call – You receive a text message that appears to come from a government organisation and asks you to urgently call a number. The person you call sounds legitimate, sounding kind and helpful. You are tricked into believing you are giving personal information for the right reasons.
Malware attack – A text message is sent with a link that installs malware onto your phone, typically a trojan horse, that captures and records keystrokes to steal passwords, contact lists and banking information.
Spear-smishing – Having collected personal information about you from social media sites the criminal sends a targeted and specific message that appears genuine. Due to the personal details held in the message the victim trusts the sender and replies with the information the criminal needs.
Vishing
Scammers call potential victims, often using prerecorded robocalls, pretending to be a legitimate company to solicit personal information from a victim. Some scammers may also record your voice and ask a question you’re likely to answer with “Yes.” They can then use this recording to pretend to be you on the phone to authorise charges or access financial accounts. Other examples of this type of identity fraud are:
AI-based vishing – A criminal can use AI to mimic a company director’s voice, convincing an employee via a phone call to transfer monies as part of a usual business process.
Caller ID Spoofing – This technique uses software to fake a legitimate caller ID such as HMRC, the police or your bank to create urgency and persuade the victim to give over information they usually would not.
Client Call – These attacks pretend to be someone new from the finance team of a client and ask for an invoice to be paid or to inform you of new bank details. This scam relies on a sense of urgency and is why an organisation should have a two-person approval process for any financial payments or changes.
Dumpster Diving – Disgarded official company documents can often have enough personal information to launch a successful vishing attack.
Robocall – A pre-recorded call through computer software, this automated call asks victims to state personal or other vital information so it can be used to steal money or open fraudulent credit cards.
Tech Support Call – More common in larger organisations where you may not know members of your IT support. Scammers will pretend your computer needs an update or repair and start asking the victim for security information like passwords, ID numbers etc.
Great to know
Social engineering and phishing scams work because they take advantage of our natural tendency to trust others. It’s easy to assume that a request for a password update or wire transfer is legitimate when it appears to come from someone we know and trust. But it’s important to remember that scammers are experts at disguising themselves and their intentions. So always be wary and take steps to verify the authenticity of any request before taking action.
Untrustworthy email volume continues to grow
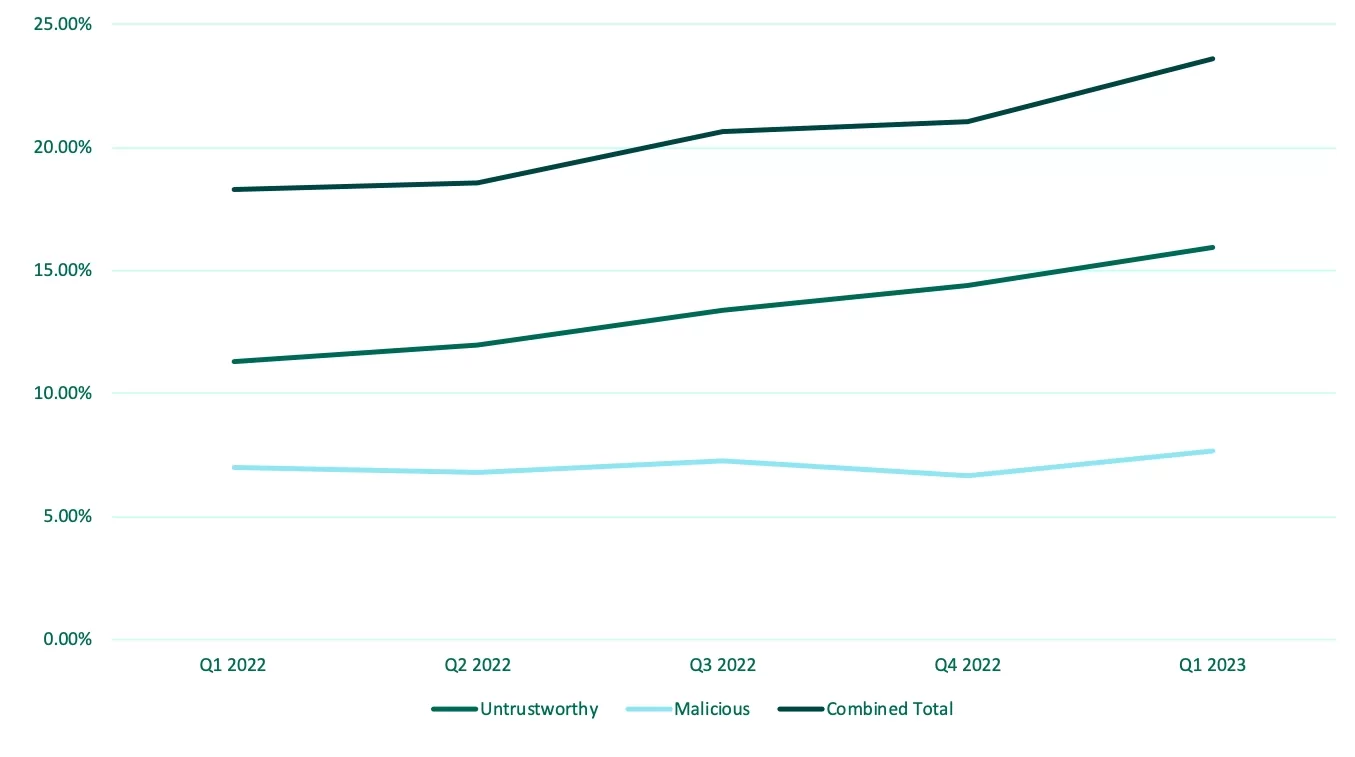
Forta’s 2023 report on BEC Trends, Targets, and Changes in Techniques states that:
“In Q1 2023, the percentage of emails classified as malicious or untrustworthy reached nearly a quarter of all messages reported by corporate users.”
To find out more about protecting your organisation from the harm of these types of scam emails give us a call at 01392 450 750 to talk to one of our experts or complete the form for a FREE workplace discovery session.






